Explain Different Approaches to Network Security
There is one critical approach for IT or network security where the sender writes their text in some specific encryption approach and the receiver reads the content by that specific decryption approach defined by a sender and only known to the receiver. You can explain the importance of adopting a.

Seguridad En Redes Wi Fi Infografia Infographic Internet Tics Y Formacion Wireless Networking Computer Security Wifi Network
But now we have explainability.

. Dialogic Teaching aims to improve pupil engagement and attainment by improving the quality of classroom talk. Trait-based personality theories such as those defined by. Explain what will be the specific approach or process that can be taken to hide the message in the case of IT Security.
Please leave a comment below and share with other students in your network if you found this explanation helpful. Personality is the characteristic sets of behaviors cognitions and emotional patterns that evolve from biological and environmental factors. Comparative politics has a long and very eminent history dating back just before the origin of systematic political.
Teachers are trained in strategies that enable pupils to reason discuss argue and explain rather than merely respond in order to develop higher order thinking and articulacy. For a long time ML models were universally viewed as black boxes because we couldnt explain what happened to the data between the input and the output. I brought the team together and explained the correct protocol to use and we.
Comparative politics is the study and appraisal of domestic politics across countries. While there is no generally agreed upon definition of personality most theories focus on motivation and psychological interactions with the environment one is surrounded by. In this article were going to explain explainability explore why its necessary and talk about techniques and tools that simplify explainability.
This incremental development is a major part of agile approaches and reflects the way that we resolve software. I was working with the security team inside our network administration department and some of our staff were managing different protocols than the rest of us. Explain why incremental development is the most effective approach for developing.
Nature and Major Approaches. You can translate user stories and propose design approaches or services to meet these needs and engage in meaningful.
![]()
What Is Network Security The Different Types Of Protections Check Point Software
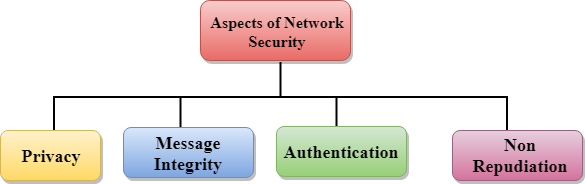
Computer Network Security Javatpoint

Indegy Ceo To Discuss Ics And Iiot Cybersecurity Approaches At S4x18 Conference Barak Perelman Wil Cyber Security Course Cyber Security What Is Cyber Security
Comments
Post a Comment